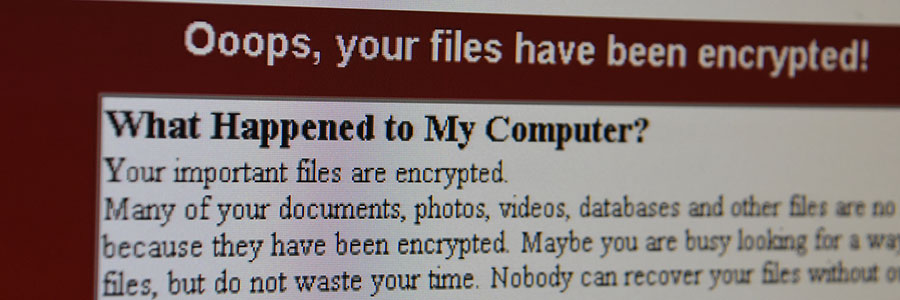
A new, Locky-type ransomware is currently infecting tens of thousands of computers worldwide. It uses the same code from the 2016 version to encrypt users’ files and it looks poised to cause another massive cyber emergency. Here’s everything we know so far. Quick facts According to a threat intelligence report, the email-based ransomware attacks started… Continue reading Locky-type ransomware is attacking systems
Locky-type ransomware is attacking systems