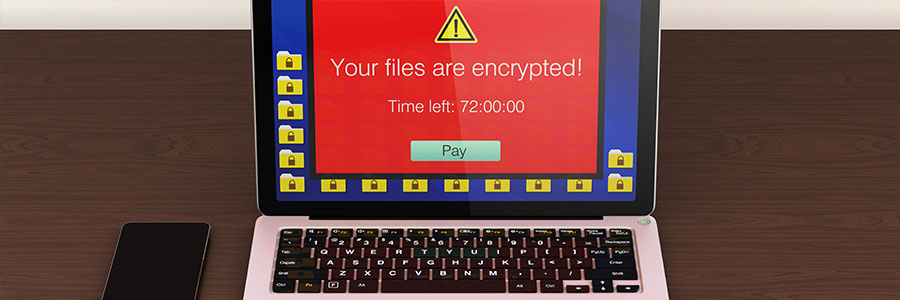
Although a ransomware infection might feel targeted, you’re not the only one who’s been infected. Ransomware is spreading at an alarming rate, but the further it goes, the more resources are allocated to fighting it. If your data is held hostage, always check these lists for free decryptors first. The state of ransomware in 2017… Continue reading No Ransom: a place for free decryption
No Ransom: a place for free decryption