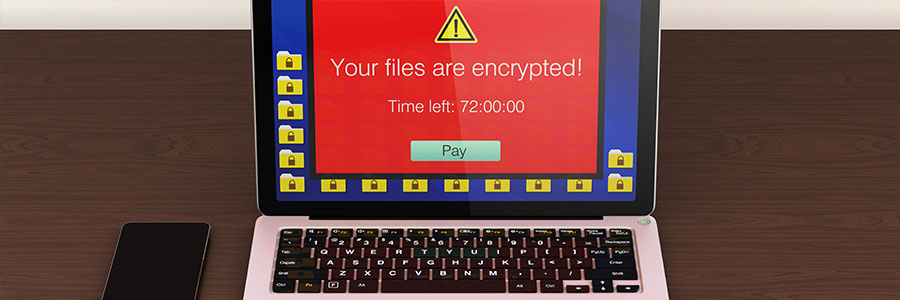
From attacks on mobile devices to ever-increasing types of malware, cybersecurity has never been more challenging. One of the best ways to stay protected is to be aware of cybersecurity threats. To that end, here are five common ways your IT systems can be broken into. 1. You are tricked into installing malicious software There… Continue reading 5 Most common security breaches
5 Most common security breaches